
It is now well accepted that virtually all brands—from the utmost recognized to the newly eager—face an unprecedented onslaught of counterfeiting and gray market trading. In emerging countries, this menace is bold and audacious, with outright fakes appearing in the open marketplace. In developed countries, the problem is similarly insidious due to online propagation of counterfeit products through e-commerce platforms.
In addition to counterfeiting, brand owners are faced with the challenge of keeping pace with the recent trend in mobile customer engagement. The digital world is rapidly changing, and eyes are now on the mobile device as the gateway for that very engagement.
The transformations now taking place in the emerging field of connected packaging can serve as a bridge to that mobile gateway and address both core requirements — protection and engagement. Here, I explore what can be achieved via a connected packaging program, along with what technologies to avoid and which ones to consider.
Engagement-driven brand protection
Let's ask a simple, though theoretical, question: How many brand owners are willing to ask their customers to check their purchase and ensure the product is genuine? The question is theoretical because although no formal studies have been carried out, the answer can surely be surmised to be as close to nil as possible. Brand owners rarely disclose that their products are under attack.
Rewarding the consumer
One way to circumvent this obstacle is to incentivize consumers to interact with the product because in return they will derive something of value. There are numerous engagement options that can be offered to consumers. One is to provide information on the product itself, guidelines on proper usage, lifestyle advice or even obtain consumer feedback. All these efforts are aimed at satisfying a basic human desire — the yearning for information and to be in the know on what they consume, what they apply to their bodies and what they keep in their homes. And that in turn can form a very powerful driver for consumers to engage with the brand because they will receive a direct and personal benefit.
Another driver for engagement is the appeal of getting something of monetary value in return for interacting with the product. One common approach is to enlist customers into a loyalty program to drive repeated purchase. Instant rewards can also represent a powerful incentive through cash back directly into the customer's digital wallet. And finally, there is the allure of winning a sweepstake prize. To turn a product into a lottery ticket not only draws customers to that brand but also in turn rewards the owner with increased sales.
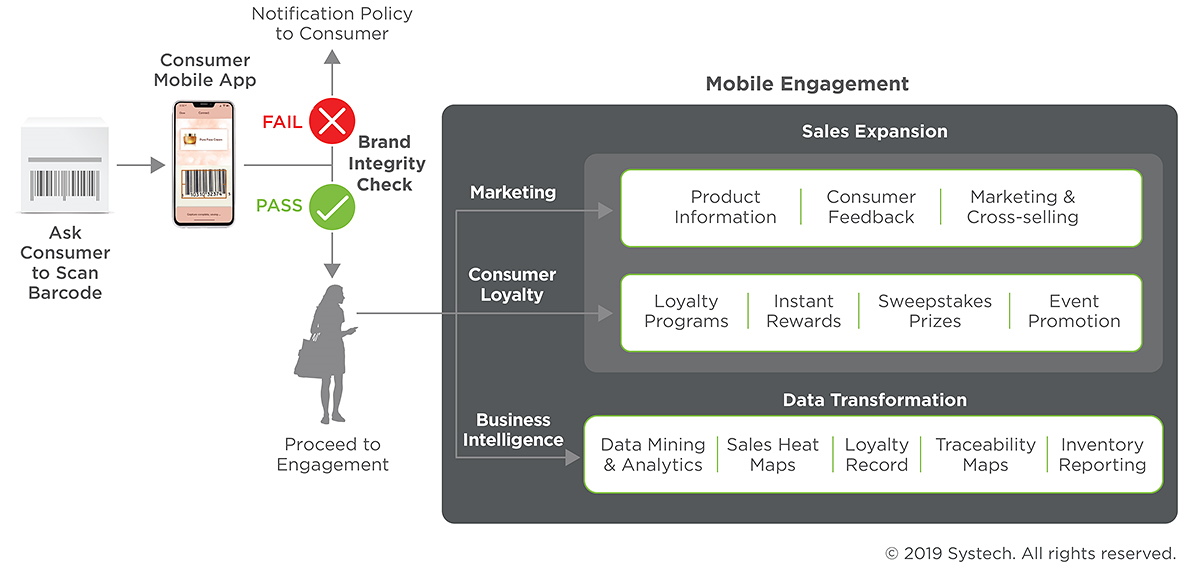
The surrogacy model
What do all the foregoing sales augmentation tactics have to do with brand protection? Consider the left side of the figure above. As shown here, the engagement portal would only unfold after the product has been verified as authentic. If not, a flag is raised, and the brand owner sends either a warning message or a request for more information. If the product is genuine, the interactive portal opens and the brand owner can deliver from a menu of engagement options.
The most important part of this solution is that the consumer is not even aware that a brand integrity check is occurring in the background. Consequently, this approach can dramatically increase the number of checks in the marketplace via a large consumer base without disclosing the surrogate nature of the protection program. Consumers are driven to interact with the product because they derive a personal or monetary benefit, all the while creating a multiplicative impact to help curb the menace of counterfeiting and gray market trading.
The BI loop
Each interaction with a product provides significant marketplace insight to the brand owner. There is a substantial amount of business intelligence (BI) data that can be mined and analyzed, such as which specific product was scanned, when that interaction took place, at what geographical location and even who the customer is. The most overt BI benefit however would be the brand protection component. The collective accumulation of adverse events would provide brand owners with actionable intelligence to undertake interdiction efforts, weed out distribution vulnerabilities and modify defense strategies.
The BI component brings the program full circle — clever engagement strategies drive authentication, that in turn amplify protection outcomes, that ultimately close the loop by giving brand owners coveted marketplace data.
The switch to digital
How can all of this be done? The older approaches to brand protection involved analog offerings where overt visual features such holograms and similar solutions represented the mainstay of what was available. None of those solutions could offer the kind of interactive engagement options described in the previous section. Instead, the current advances in connected packaging are being driven by digital technologies.
Fingerprinting – the new wave in item-level digitization
The fundamental requirement for brand owners can be stated as follows:
- give them the means to engage with their customers to provide information or reward;
- ensure it is executed through a packaging technology that cannot be cloned or reverse-engineered by counterfeiters;
- use the reward-information gateway to create a surrogate means for brand protection;
- and do all this (if possible) without changing or adding anything to the package.
The latter is a highly coveted requirement because brand owners are averse to placing an extra barcode or any additional feature onto the artwork of their perfectly designed package.
The above requirements represent a very tall order indeed. As it happens, the march of technology has created the good fortune to now provide a solution that meets all these demands. Known generically as fingerprinting, the idea is that a component of the package artwork contains a unique noise pattern that is not discernible to the human eye but can be detected by a smartphone camera. No two packages will have the same noise pattern and therefore this feature serves to distinguish each and every individual package.
It is this unseen noise that is authenticated, and which cannot be successfully replicated by a counterfeiter even if the package is perfectly copied. Once the noise signal is authenticated, a gateway can then open to engage the consumer. And given that the noise is already an inherent component of the package, nothing needs to be added to the artwork. All that remains is to find a way to capture, store and authenticate the noise that is intrinsically present in every package.
A revolution in engagement-driven brand protection
An ideal solution would be one where the linear barcode that is present on all consumer packages provides the locus for the covert noise. This is the exact solution that has been developed by Systech, providing the only offering where a common feature of the package artwork is used in the fingerprinting process.
As shown in the figure below, Systech places a camera and associated devices needed to image the barcode either on the packaging line or at the package supplier location. Once the barcodes are fingerprinted through Systech's platform for a given program, they are stored in a secure cloud. The products can then be released into the marketplace where both authentication and engagement activities can unfold via a smartphone application.
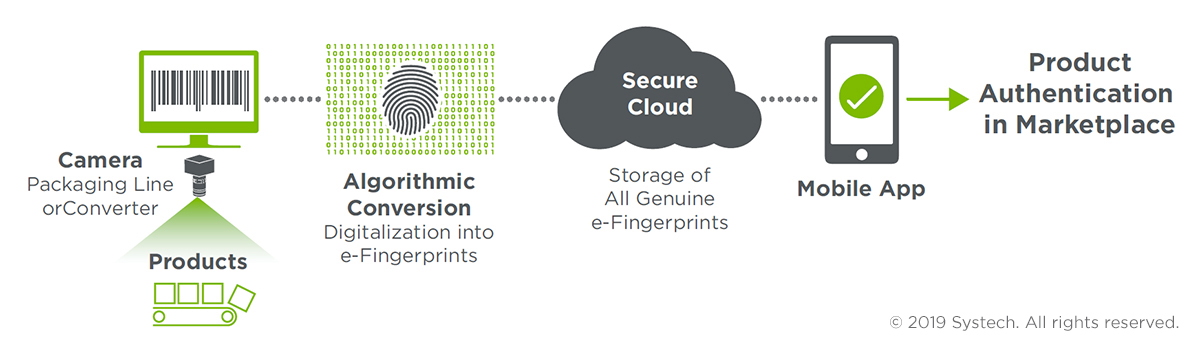
This approach offers all the desired requirements as explained above, with the additional benefit that using the linear barcode bypasses the need to apply an additional token or taggant on the package. The brand protection program can then be delivered in a surrogate manner through a consumer engagement design.
The noise in the marketplace
The current brand protection landscape is filled with a multiplicity of providers all portraying the superiority of their solution. How then does a brand owner parse through this noise to arrive at a worthy solution for adoption? There are three elemental but essential guidelines to keep in mind.
Choose digital – There is no upside to choosing an analog solution nowadays if the objective is to protect brands and consumers with the additional goal of initiating consumer engagement immediately or as a later calling.
Choose fingerprinting — Fingerprinting technologies provide supreme security assurance because the noise signal in an original package simply cannot be replicated. Consequently, a well-designed fingerprinting program can provide the ultimate confidence for safe launch of a consumer engagement program in the public marketplace.
Choose experience — Selecting a technology that combines authentication with engagement must be a careful and thoughtful exercise due to the high stakes in play. Although fingerprinting represents an excellent choice, it is equally important to choose a vendor with an excellent track record of delivering brand protection success to provide the necessary security assurance that comes through longevity.

Many leading brands across diverse product categories rely on Systech to secure their supply chains. Its brand protection suite provides the only non-additive digital fingerprinting solution based on the linear barcode. Once deployed, Systech provides the most secure platform for an engagement-driven and surrogacy-mediated brand protection program. Systech brings a level of proven expertise to keep products authentic, safe and connected across the supply chain.
Choosing digital and choosing fingerprinting offers the best option for protecting brands and engaging consumers — a perfect combination of opportunity delivered through connected packaging. And when it comes to selecting the most trusted provider of these solutions, there is only one answer… choose Systech.
To learn more about connected packaging opportunities—download The Promise of Connected Packaging white paper.
Avi Chaudhuri is Chief Scientist, Systech
©
SecuringIndustry.com







