Viewpoint: The emerging barcode initiative for medicines in India - part 2
Avi Chaudhuri, PhD, 29-Sep-2022
Part 2 – Developing a solution architecture that is both feasible and eliminates counterfeit medicines
India is now steadfastly moving toward the creation of a massive new regulatory framework to curb the troubling growth in counterfeit medicines. The newly issued draft regulations by India’s Ministry of Health and Family Welfare (MoHFW) will require placement of a 2D barcode on drug packages [1]. This effort is widely viewed as a positive measure that complements a parallel attempt to protect export medicines that was launched a decade back by the Indian Ministry of Commerce.
It is expected that revisions to the MoHFW regulation will take into account market feedback to avoid design mistakes made in other programmes. This article, the second in a three-part series, is based on the simple predicate that an impactful regulatory mandate has really just one chance to get it right. In that spirit, the previous article, titled Part 1 — How changes to the draft guidelines can set the foundation for a successful anti-counterfeiting programme, focused on why certain changes to the draft regulation are necessary to prevent later failure [2].
Whereas Part 1 covered fundamental issues related to barcode content*, with technical details more suited to regulatory and solution specialists, this article will build on those recommendations to outline a general solution architecture for product coding and its applicability. Here, I will take a more pedagogical approach so that a wider audience can understand key programmatic factors necessary for launching successful anti-counterfeiting campaigns in a large and complex market.
Key takeaways from Part 1
Part 1 of this series addressed the structural elements of the draft MoHFW regulation and identified three concerns with regard to barcode content and formatting where recommended revisions would ensure that a proper foundation is put in place for sustaining a successful programme, as follows.
- The proposal for embedding eight data fields into the barcode should instead be reduced to only those that are widely used. In certain cases, the barcode could contain just two elements (GTIN and serial number), with overprinting of batch number and expiry date.
- Ensure use of GS1 standards for barcoding (DataMatrix), product identity (GTIN) and content formatting rules using application identifiers.
- Incorporate serialization in the programme so that each saleable package is endowed with its own unique serial number.
A major loophole in the draft regulation was also identified that could upend the entire programme. By allowing manufacturers to bypass barcoding of primary packages due to space constraints, the programme could permit virtually all blister packs to evade the barcoding requirement. Such an outcome would allow counterfeiters to continue their trade without the hindrance of having to confront any required security features found on original products.
The key takeaway from Part 1 is that an effective anti-counterfeiting programme must start with placement of a serialized barcode on all saleable medicine packages, including blister packs, and that the barcode should be constructed using international standards and well-established practices in terms of content and formatting. Once done, the core foundation for the Indian programme would be in place from which next steps in creating an effective programme can be developed. Those steps are taken up in the remainder of this paper.
Two (very) different concepts of consumer protection against counterfeit drugs
A serialized barcode can subserve two programmes that are very different in nature, as illustrated in Figure 1. The starting point is to apply the barcode either through direct printing or label application (1) upon the saleable package, whether it is a bottle, carton, blister or vial (2). Once coded, the product flows through multiple waypoints, such as distributors and stockists, on its way to the final retail outlet (pharmacy), clinic, or online marketplace.
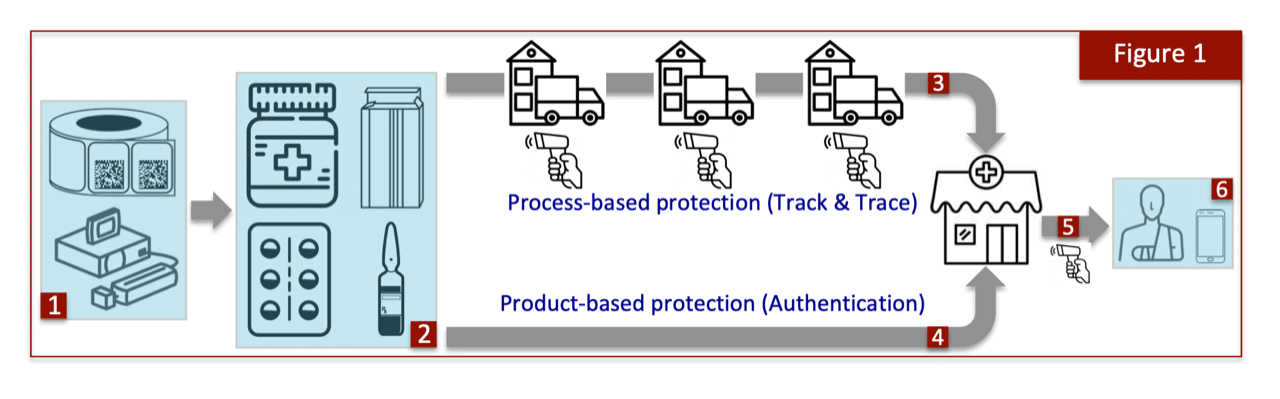
One view of how to protect against counterfeiting is to know exactly how the medicine pack made that journey and to document who held the product, where, and for how long. This process-based solution is called Track & Trace because the medicine pack is tracked along its entire journey by capturing the barcode and uploading all ownership information into a centralized record (3). In reality, individual packages are not themselves tracked but rather an aggregated digital tree is first created at the manufacturing site spanning larger hierarchical enclosures, all tagged through the serialized barcodes at each level that allows the parent containers to instead be tracked.
The logic behind the Track & Trace approach is that exact knowledge of a drug’s journey through the supply channel will make it difficult for counterfeiters to make an entry because of mandatory ownership recording at each node. The tracking pedigree will therefore fully encompass the electronic chain of custody of that drug’s journey, allowing any adverse events to be either detected immediately or traced back to the origin at a later stage. The United States adopted this very approach in 2013, known as the Drug Supply Chain Security Act (DSCSA), to create one of the most ambitious drug protection undertakings, and whose full implementation is still unfolding.
A very different approach to protection against counterfeit drugs is to implement a product-based solution, generally referred to as Authentication, where again the serialized barcode on the saleable drug package serves as the gateway to the programme. Unlike Track & Trace, a product-based approach is unconcerned with tracking the product through the supply chain, and in fact is not even troubled with how a product arrives at the dispense point (4).
A key feature of this approach is empowerment to verify the drug’s serial number. The European Union has set up a programme along these lines, known as the Falsified Medicines Directive (FMD), that requires the dispensing agent to authenticate the serial number via a central database before sale to a customer (5). The logic is that a verified serial number would by extension confirm the drug’s authenticity. A further extension of this approach is to actually empower consumers so that they have the ability to verify the drug package themselves, say by scanning the serialized barcode with a Smartphone (6). This tantalizing possibility is further explored in the next section.
What is the right solution for India?
The question that next arises is which of the two protection regimes described above is best suited for India — Track & Trace or Authentication. The two are not mutually exclusive but all national programmes generally adopt one approach to fulfill their requirements. And here it seems that the MoHFW has given its preference by stating that drug manufacturers are to use the barcode in conjunction with a “software application to facilitate authentication.” The term Track & Trace is not found anywhere in the draft regulation. The choice of Authentication as the designated framework for India is a very wise move on the part of the government, as explained next.
Launching a Track & Trace programme in any market is fraught with challenges, the most serious being the complexity of the operational structure. As shown in Figure 1, all supply chain accomplices are engaged in the programme, and in fact, participation is mandatory. In the absence of a federal law forcing such participation, as is the case in the United States, there would be utter chaos and programme failure. No such law exists in India, nor is one being contemplated.
The highly dispersed drug distribution system in India imposes a further compliance burden, with stockists numbering in the tens of thousands. The cost and complexity of having all participants willfully engage would be an untenable proposition. And yet, there are frequent claims by various Indian vendors of their ability to provide a full Track & Trace solution, claims often made with passionate ignorance of the details involved or the myriad intricacies of implementation.
An authentication programme would be hands down the best way to proceed for India, and kudos to the MoHFW for that awareness. But that does not mean it can be unfurled without a comprehensive strategic plan, a sound architectural framework, and careful consideration of possible loopholes. It was difficult to find those details in the MoHFW draft. The guidance that follows is based on recognition that India now has the opportunity to create one of the most outstanding drug authentication programmes anywhere by capitalizing on its unique market conditions.
An important decision at programme outset
The design of an authentication programme for India must however first answer a fundamental question — who will be doing the authentication? The European programme is based on retailer verification at time of product dispense, as shown in Figure 1. Could this work in India? Yes, but not at the beginning. The problem again comes down to the sheer size of the Indian market with over eight hundred thousand pharmacies [3], the time needed to create a legal mandate for adoption, and the ensuing delay due to likely pushback from a powerful lobby. A further delicate concern is that some retailers may actually be co-conspirators in the counterfeiting scheme.
A truly unique programme that India can launch here is to instead empower consumers at the very outset via a Smartphone-based authentication regime. Such an outcome is operationally well suited for this market and would also have a trailblazing effect, for several reasons. First, the very idea of scanning a barcode is already an intrinsic feature of the country, driven by the ubiquitous use of digital wallets, code-based loyalty programmes, and interactive mobile marketing schemes — all complemented by the fact that over 85% of the population will soon have a Smartphone [4].
Second, the larger the authentication base, the more success it would have in terms of creating psychological deterrence due to the multiplicative impact. Imagine that a subset of consumers purchasing medicines at a particular outlet engage in the authentication exercise. The Indian government would in effect be unleashing millions of “inspectors” in the marketplace at no extra cost, each with a zealous determination to ensure they are not being duped or having their health and safety compromised. How many retailers will want to engage in nefarious practices with the foreknowledge that their next sale could possibly lead to instant interdiction?
And third, the very idea of empowering consumers to have assurance on a purchase as important as their medicine would create powerful resonance across the country. The positive politics of such a plan would have excellent benefits in terms of broader societal support. There is nothing better than giving power to the masses, more so in the world’s largest democracy.
There is one caveat however — counterfeiters, having made major investments in their trade, will do everything in their power to protect their business by finding possible loopholes to defeat the new threat. That is a hard lesson we have learned over the years through multiple episodes in many markets. The challenge then is to find a way to create a consumer-based authentication programme that will thwart those unwavering counterfeiters. Let’s however first ask a fundamental question.
What can a counterfeiter do to defeat an authentication programme?
It is important to first analyze where a security programme based on serialized barcoding can go wrong by simulating its points of vulnerability. It turns out that committed counterfeiters will have only three options at their disposal, all of which can be countered through careful design.
1) Create fake serial numbers, embed them into a barcode and populate the marketplace
The fact that all barcodes are undecipherable by human vision means that counterfeiters can freely embed false data into their own version, place it on fake products, and dispatch into the market. One version of this idea is to embed bogus GTIN or serial numbers. The fake package will appear as being normally barcoded, except that it contains nonsense data.
2) Create fake barcodes that redirect consumers to their own servers for authentication
This effort is similar to that above. However, instead of merely placing false data into a barcode, the idea is to send consumers to the counterfeiter’s own site where of course all verification outcomes are positive, often recreating the actual brand owner’s messaging, images and all. This act represents one of the most sinister counterfeiting efforts because it is often difficult to detect and therefore remains under the radar.
3) Create exact multiple replicas of original product barcodes
The final effort is the most simplistic of all and yet can produce dire consequences. The counterfeiter obtains an original product and proceeds to replicate the exact same code on multiple fake products. The duplication is usually done in small numbers because of the greater detection likelihood with a large-scale effort. The emerging concern is that criminal enterprises have largely migrated from lifestyle to life-saving drugs [5]. The higher cost of these medicines can therefore pay large dividends to counterfeiters even at small volumes.
The foregoing possibilities are not just theoretical but in fact now commonly found in various Asian markets [6-8]. There always remains the additional prospect of a corrupt supplier or solution provider who creates a parallel channel of duplicate codes or security labels for distribution to a counterfeiter. That problem is however far less common, though not unheard of [9].
We now take up the challenge of designing an effective consumer-based authentication programme for India that will thwart committed counterfeiters against the possible scenarios described above.
An authentication programme for India that is both feasible and impermeable to counterfeiters
A conceptual architecture for a comprehensive programme designed specifically for India is outlined in Figure 2. The first essential requirement is to ensure that only one Smartphone application, to be developed by the government sponsor, is used in the programme. It is essential that the general public come to understand that all drug verifications in the marketplace are to be undertaken only through the “government” app so that the opportunity for mirroring by other parties cannot even arise.
The authentication exercise begins by scanning the barcode on the drug (1). The agency would then receive the scanned data through a link built into the app (2). However, rather than the agency performing serial number verification, that process will instead be relegated to the brand owner. An internal lookup table maintained by the agency would guide the transfer process to the product’s correct owner, as identified through the GTIN (3). Once the owner is identified, a link is sent back to the app (2) at which point the consumer is automatically transferred to the brand owner (4). The serial numbers are only retained by the product’s owner and therefore it alone is responsible for the code verification step and sending the outcome back to the consumer, with copy to the agency (4), as to whether authentication was successful or not (5). The brand owner can select a solution provider of its choice to execute its share of the programme.
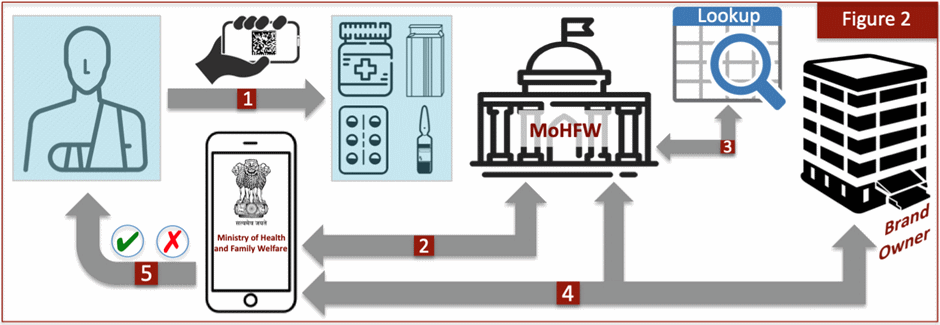
The scheme described here has several advantages. First, a public-private partnership model for complex programmes is now becoming accepted as a worthy framework in many emerging markets. Second, a division of labour between the agency coordinating the authentication activity and brand owner verifying the code would result in a more streamlined process. Imagine if the agency had to be responsible for maintaining a database of literally hundreds of millions of serial numbers, and then issuing authentication results from that database. The bottleneck would cause immense consumer frustration due to delayed response times. A distributed model for the verification step would represent the best option for agile outcomes. Third, brand owners are well positioned for undertaking code verification because its own solution provider would also issue serial numbers for its various products, thereby avoiding the cumbersome process of uploading huge volumes of numbers to the agency’s server.
The main benefit of the proposed framework is that it creates strong firewalls and high deterrence against counterfeiting. The programme is protected from the first possible attack discussed above (i.e., counterfeit products with false serial numbers) due to the activity in Step 4, where the brand owner verifies an incoming query against a database of its own issued serial numbers. A bogus serial number would fail verification at this stage. Furthermore, a bogus GTIN would be unrecognized by the agency and fail at Step 3.
The most potent threat to any anti-counterfeiting programme would however come from the second possible attack — i.e., fake barcodes that direct consumers to the counterfeiter’s own site. Here too the solution presented in Figure 2 offers total protection because of the fact that consumers would only use the government verification app where inquiries are processed only by the sponsoring agency. A spurious barcode will therefore fail at Step 1. Under no circumstances could a fake barcode containing a bogus link, GTIN, or serial number bypass the security firewall.
That leaves us with the third attack possibility — i.e., creating exact multiple replicas of a genuine barcode. This is the perfect crime because the app will capture a valid GTIN and serial number, and therefore the process in Figure 2 will unfold without hindrance. It is not possible to distinguish a fake from a genuine product when they both contain an identical barcode. Although there are ways to mitigate this threat, such as by freezing the code once the problem is detected, it remains a fact that at least one fake product (and perhaps more) will pass through. What’s more, the fake drug will create false reassurance because a positive verification outcome is sent to the hapless consumer who unfortunately happened to make that particular purchase.
It is now well acknowledged among security professionals that serialized barcodes are susceptible to faithful duplication, a fact that has greatly diminished the earlier enthusiasm for their use. The programme design illustrated in Figure 2 would nevertheless provide sufficient protection for most pharmaceutical products in the non-prescription category where counterfeiting is more limited. However, those medicines that fall in sensitive categories or which are particularly vulnerable due to their value will require an additional protective layer, as discussed next.
An adjunct “copy-proof” technology to detect barcode replication
One of the biggest developments in the field of anti-counterfeiting is the appearance of an entirely new generation of technologies that work in conjunction with barcodes to make them “copy proof”. Of course, anything can be copied and certainly counterfeiters will not hesitate to pursue every possible means to maintain their business, including outright replication of a genuine code. A better tagline to these new technologies is that they are nonclonable. In other words, a copied version will not survive authentication and therefore will be flagged as being compromised.
The last five years has seen a proliferation of these technologies. One particularly acclaimed genre is known as fingerprinting, an apt term because an original product can be endowed with a graphical feature that serves as its own unique fingerprint and, unlike a barcode, cannot be recreated or copied by any means to successfully evade detection. The inclusion of a fingerprint token in the programme described here would provide ultimate protection against false coding, phantom links, and outright duplication — the full trio of counterfeiting possibilities.
The insertion of an adjunct nonclonable feature can be undertaken by the brand owner with freedom to choose from a palette of options. The architecture presented in Figure 2 would in fact make it quite straightforward. The brand owner can simply add an extra step after handover from the agency (Step 4) to protect the subset of its portfolio that is particularly vulnerable. Regulatory consideration is also strongly recommended for requiring this additional technology layer for the so-called Schedule H drugs (those requiring a prescription), H1 drugs (a subset that includes particularly sensitive products), medicines containing controlled substances, and those that have been specifically targeted for counterfeiting.
The path to choosing an adjunct technology, either voluntarily or through compliance, should ensure that the following five requisite features are present.
- Nonclonability — the technology must be truly nonclonable and survive any efforts at duplication by even the most advanced means. All copied versions must be flagged as suspect without reservation.
- Mobile authentication — authentication must be permissible only through mobile phone devices, including all Apple and Android phones minimally introduced in the past five year, that provides a binary response only — successful or suspect.
- Unlimited authentication allowance — the nonclonable technology must permit unlimited authentications without any imposed restrictions or the requirement for credentialization.
- Offline capability — the technology must permit authentication even in the absence of a cellular network or mobile Internet service.
- Static graphical feature — the technology should ideally be a static token whereby the exact same feature is replicated on all packages or security labels in order to simplify implementation and reduce cost.
The inclusion of a nonclonable token is certainly not necessary for the majority of drugs in the Indian market, which would in any case be well served by the serialized barcode programme proposed here. However, it is unquestionable that a certain subset of the market will need to be additionally protected due to likely attacks from code duplication. This vulnerable drug group is ripe for counterfeiting and therefore should be endowed with an additional level of protection that simply cannot be compromised.
Summary
A fundamental concept in consumer protection is that the saleable item must itself contain something that can be used to secure it. And that something must be a tool that can decisively tell the buyer that it is indeed the genuine article. It is this clear objective that leads to the strong recommendation for India to pursue a purely authentication-based anti-counterfeiting programme rather than a Track & Trace initiative. Indeed, the size and complexity of the Indian drug market, coupled with public yearning for empowerment, makes clear that a consumer-based programme that transfers verification power to the people would yield programmatic and political success.
That success can however be short lived in the absence of thoughtful programme design. There is nothing worse than providing false reassurance to a patient — in other words, providing notification that a drug is genuine only to later discover that it was in fact a counterfeit variant. Such occurrences can have a killer effect on a programme rolled out with marketing fanfare, consumer adoption, and costs imposed on manufacturers. It is for that reason alone that considerable effort has been made in this article to offer solution possibilities that thwart future counterfeiting efforts.
The majority of drugs in the Indian market can be successfully covered via a serialized barcoding regime, which if well designed can have excellent outcomes in protecting the public. The solution proposed here is based on public-private collaboration to create a distributed framework where the government agency (MoHFW) serves as the gateway for directing all authentication activity mediated by the brand owner. The addition of a further layer incorporating a nonclonable technology can provide substantially added protection to a subset of medicines that fall into sensitive categories or which are particularly vulnerable to counterfeiting.
The programme architecture for the MoHFW programme offered in this paper is reliant on certain necessary amendments offered in the first article relating to barcode construction and content. What therefore remain to be covered are certain focal details around operationalizing the programme. In the next and final article of this trilogy, I will take up core implementation details that will tie together the components of the general architecture offered here to create a holistic national anti-counterfeiting programme for India.
References
[1] https://medicaldialogues.in/pdf_upload/qr-code-178763.pdf
[3] https://www.statista.com/statistics/1027563/india-retail-pharma-market-size/
[7] http://www.chinadaily.com.cn/opinion/2017-03/02/content_28400890.htm
* The use of the generic term barcode throughout this article refers only to the two-dimensional barcode that has been proposed by the MoHFW, and not the linear barcode used for retail scanning found on all packages.

Dr Avi Chaudhuri is founder of The Kulinda Consortium, a global alliance of solution providers that focuses on emerging nations to protect their citizens from counterfeiting, illicit trade, and revenue loss. His work in this field began when he became the victim of a counterfeit drug while traveling in India nearly two decades ago.
Dr Chaudhuri introduced the very concept of serialization to the Indian pharmaceutical industry in 2007, which later set in motion India’s drug export serialization programme. He is an acclaimed expert in the field of anti-counterfeiting, working with both governments and the private sector.
Related articles:
- Viewpoint: The emerging barcode initiative for medicines in India - part 1
- FDA data highlights continuing threat from fake meds; study
- India mandates QR codes on medicine APIs from next year
- Falsified rare disease drug Soliris found in supply chain
- WHO warns of falsified COVID-19 vaccines, remdesivir
- Tech Mahindra taps StaTwig for blockchain tracking of vaccines
- OECD says fakes make up 2.5 per cent of global trade
- Zydus Cadila launches verification app, initially for COVID drugs
- Illegal remdesivir on sale in India as COVID tightens its grip
- India extends aggregation deadline for drug exports again
- India to set up panel on drug authentication mechanism
- India sees ‘alarming’ 24 per cent rise in counterfeit incidents

Click here to subscribe to our newsletter
29-Sep-2022
Related articles:
- Viewpoint: The emerging barcode initiative for medicines in India - part 1
- FDA data highlights continuing threat from fake meds; study
- India mandates QR codes on medicine APIs from next year
- Falsified rare disease drug Soliris found in supply chain
- WHO warns of falsified COVID-19 vaccines, remdesivir
- Tech Mahindra taps StaTwig for blockchain tracking of vaccines
- OECD says fakes make up 2.5 per cent of global trade
- Zydus Cadila launches verification app, initially for COVID drugs
- Illegal remdesivir on sale in India as COVID tightens its grip
- India extends aggregation deadline for drug exports again
- India to set up panel on drug authentication mechanism
- India sees ‘alarming’ 24 per cent rise in counterfeit incidents
Sponsored Content
The Dark Side of Imitation – Counterfeit Alcohol and the Fight for Safety
The Transported Asset Protection Association (TAPA) has published a white paper on the scourge of counterfeit alcohol in response to a string of high-profile incidents that have claimed hundreds of lives.
The document details some of the most notorious incidents in recent years and explains how a brand protection standard (BPS) developed by TAPA Asia Pacific (TAPA APAC) can strengthen the supply chain against counterfeit goods by encouraging logistics companies to "design out" vulnerabilities. Read more
Sponsored Content
The Dark Side of Imitation – Counterfeit Alcohol and the Fight for Safety
The Transported Asset Protection Association (TAPA) has published a white paper on the scourge of counterfeit alcohol in response to a string of high-profile incidents that have claimed hundreds of lives.
The document details some of the most notorious incidents in recent years and explains how a brand protection standard (BPS) developed by TAPA Asia Pacific (TAPA APAC) can strengthen the supply chain against counterfeit goods by encouraging logistics companies to "design out" vulnerabilities. Read more
Press Releases
-
》 Energous introduces battery-free e-Sense tag, establishing first end-to-end wireless power platform for the ambient IoT
-
》 TrusTrace launches 4th industry playbook: A new framework to streamline data collection to comply with industry regulations and de-risk supply chains
-
》 Crane Authentication unveils InsightPulse: A discreet, smartphone-enabled authentication system
-
》 Antares Vision Group partners with Siempharma to enter pharma labeling equipment market with automatic unit for cylindrical containers
Partners



